MySQL vs MongoDB (NoSQL) database MongoDB vs MySQL: Comparison Between Relational and Document Oriented Database Both are used for storing the data and free to use that is both comes under open-sources software. MongoDB might be unfamiliar at least to some of us as it is a relatively new compared to other established databases…
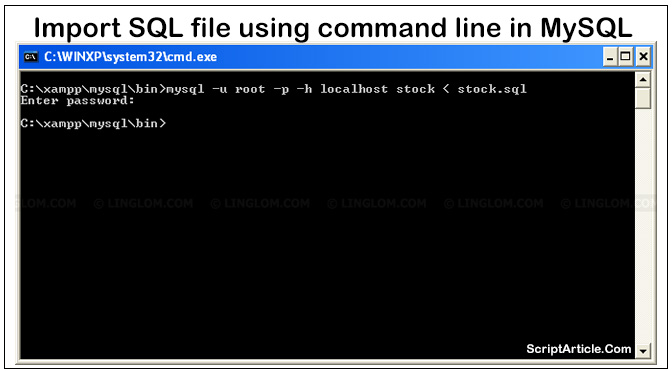
Import MySQL database using command line If you have a very large SQL dump file to import and you know very well that it is not very easy to import using phpMyAdmin, even if you split it in many pieces, it is also be hard using PHP script as it will time out after…
Basic principles of Web application security Some general principles of web security, every web developer needs to know. As we all know PHP make us rich in internet based application and we are surrounded by a lot of applications and almost all types. As the popularity increases and attacker(threats) also increases in same proportion. …
Search Engine Spider and User Agent Identification with “Ultimate User Agent Blacklist” A user-agent is software (a software agent) that is acting on behalf of a user. In many cases, a user-agent acts as a client in a network protocol used in communications within a client–server distributed computing system. For more information view…
First of all, there is no benefit of disabling plugin updates. It is very important as I have previously said in the posts that you should keep your WordPress version as well as plugins up to date. If you don’t keep, then your site could be susceptible to security vulnerabilities or performance issues. …
You can prevent spaces and specific unwanted sub strings in WordPress usernames (restrict usernames wordpress), you have to prepared a regexp for this. Prepare your regular expression and use the same in the below function. After that put this function in your theme’s “functions.php” that’s it. //Custom Function /* * add a filter to…