Basic principles of Web application security Some general principles of web security, every web developer needs to know. As we all know PHP make us rich in internet based application and we are surrounded by a lot of applications and almost all types. As the popularity increases and attacker(threats) also increases in same proportion. …
If your site is hosted on Shared Server and you want to use Zend library on your project. For Dedicated server, you have full root access and can have remote or full putty access of your server, you can install/uninstall any library as well as software in the server. The same will be done…
Prevent gaps/holes in a MySQL table AUTO_INCREMENT Primary Key field. Generally during the MySQL database development you create tables with a Primary Key, a very simple way to create a primary key is make it Auto-increment and unsigned integer with Not Null property right? I think most of you generally follow the above…
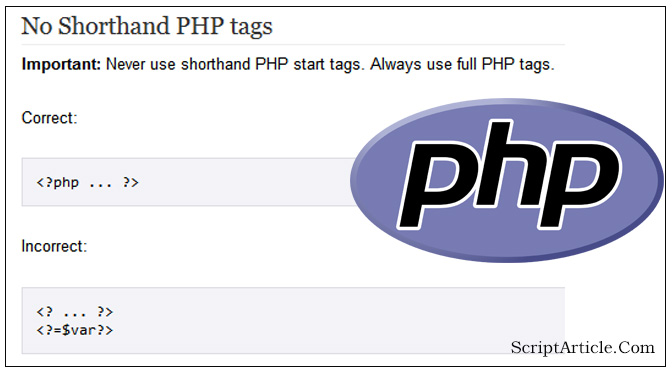
After a fresh installation you could find that PHP short_open_tag disabled by default in php.ini file. You can check by using phpinfo() PHP function. Under PHP Core setting you can find as below Directive Local Value Master Value short_open_tag Off Off If “short_open_tag” is found off in your php.ini file then you…
Most of us (Web Developer) use JQuery during the development, if you are not aware about the jQuery or interested in any other JavaScript Library then below is just a very quick overview about the jQuery. “jQuery is a fast, small, and feature-rich JavaScript library. It makes things like HTML document traversal and manipulation,…
Fixed: PHP move_uploaded_file() and copy() function is not uploading the file In the programming field we usually need to upload the files in the folders. In PHP, we have 2 functions for the purpose. 1st is move_uploaded_file() 2nd one is copy(). I think you know well, what the difference between these two copy() vs…